Pi-hole FTL v5.8, Web v5.5 and Core v5.3 released
As always, please read through the changelog before updating with pihole -up.
Highlights
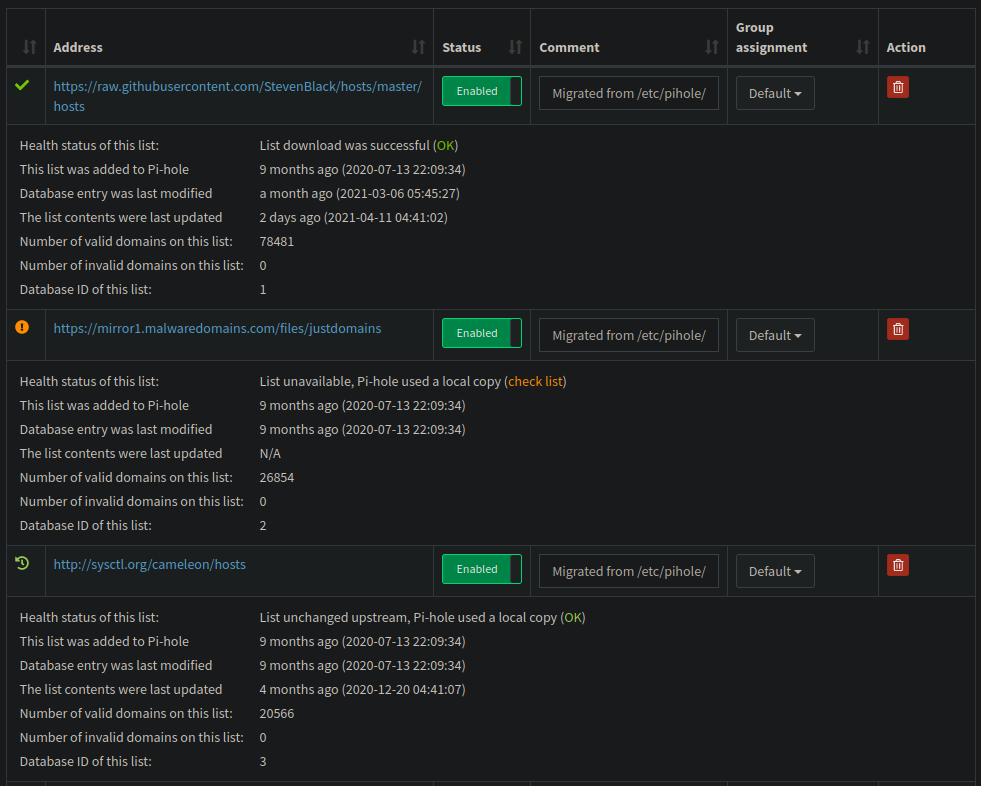
More details for your adlists
The web dashboard does now provide health-status and statistics about downloaded and processed adlists. You can see when they were last downloaded, when they were last changed and it they work at all or contain invalid domains. This aims at simplifying using additional lists.
Add Pi-hole darker theme
This PR adds a third default theme, an even `darker` variant of the dark one. It also fixes an issues with the existing `dark` theme where links in box headers (like the Query Log’s “show all”) were completely invisible.
Comparison between the existing dark (on the left) and the new darker (on the right):
Automated IP blocking mode
Until now, FTL’s IP and IP-NODATA-AAAA blocking modes sourced the IP to deliver on a blocked domain from the setupVars.conf values IPV4_ADDRESS and IPV6_ADDRESS. This is, however, quite a limitation, especially if the device running Pi-hole has more than one interface or of the address is changing. To address this, FTL v5.8 implements an automated IP blocking mode. Instead of reading the addresses from setupVars.conf, we dynamically determine the address of the interface a query arrived on. We then use this IP address in the blocked reply. This does not only reduce maintenance (IPV4_ADDRESS and IPV6_ADDRESS can now be removed from setupVars.conf) but also localizes blocked queries. The automated detection can be overwritten using REPLY_ADDR4 and REPLY_ADDR6 in pihole-FTL.conf.
Update embedded dnsmasq to v2.85
New features, bug fixes and several other tweaks are contained in this release. Check out the change log below for more information.
FTL CHANGELOG
- Automate IP blocking mode #965
- Simplify handling of
.luaand.dbfiles #1086pihole-FTL something.lua
automatically launches the embedded LUA enginepihole-FTL something.db
behaves the same way assqlite3 something.db- Similar things like
pihole-FTL something.db "SELECT * FROM abc;"
are possible as well
- Add more regex warnings to message table #1092
- Circle CI: skip uploading build artifacts on forks #1093 (thanks @bershanskiy)
- Update SQLite to 3.35.4 #1083 #1089 #1097
- Various enhancements and a few memory-leak fixes #1084
- Resize shared memory only when locking #1072
This is not really a functional change, however, it makes the code more read- and understandable in some places. - Escape DHCP options if necessary #1070
- Ensure FTL can be compiled from static tarballs #1091
- Use properly-sized buffer for format_time() #1088 (thanks @bershanskiy)
- Fix
pihole-FTL testnot terminating properly (noticed in adockerenvironment) #1067 - Fix incorrect “FATAL: Trying to access upstream ID -1” warning in the logs #1061
- DNS server improvements:
- Fix problem with DNS retries in earlier versions.
The new logic in 2.83/2.84 which merges distinct requests for the same domain causes problems with clients which do retries as distinct requests (differing IDs and/or source ports.) The retries just get piggy-backed on the first, failed, request.
The logic is now changed so that distinct requests for repeated queries still get merged into a single ID/source port, but they now always trigger a re-try upstream.
To avoid excessive spamming of the upstream server, similar queries are collected for up to two seconds when the query has already been sent upstream. All clients will get replies when the answer comes back. - Avoid treating a
dhcp-hostwhich has an IPv6 address as eligible for use with DHCPv4 on the grounds that it has no address, and vice-versa. - Add
dynamic-hostoption
AandAAAArecords which take their network part from the network of a local interface. Useful for routers with dynamically prefixes. - Teach
bogus-nxdomainandignore-addressto take an IPv4 subnet. - Use random source ports where possible if source addresses/interfaces in use. CVE-2021-3448 applies.
It’s possible to specify the source address or interface to be used when contacting upstream name servers:server=8.8.8.8@1.2.3.4orserver=8.8.8.8@1.2.3.4#66orserver=8.8.8.8@eth0, and all of these have, until now, used a single socket, bound to a fixed port. This was originally done to allow an error (non-existent interface, or non-local address) to be detected at start-up. This means that any upstream servers specified in such a way don’t use random source ports, and are more susceptible to cache-poisoning attacks.
We now use random ports where possible, even when the source is specified, soserver=8.8.8.8@1.2.3.4orserver=8.8.8.8@eth0will use random source ports.server=8.8.8.8@1.2.3.4#66or any use ofquery-portwill use the explicitly configured port, and should only be done with understanding of the security implications. Note that this change changes non-existing interface, or non-local source address errors from fatal to run-time. The error will be logged and communication with the server not possible. - Change the method of allocation of random source ports for DNS. Previously, without min-port or max-port configured,
dnsmasqwould default to the compiled in defaults for those, which are 1024 and 65535. Now, when neither are configured, it defaults instead to the kernel’s ephemeral port range, which is typically 32768 to 60999 on Linux systems. This change eliminates the possibility thatdnsmasqmay be using a registered port > 1024 when a long-running daemon starts up and wishes to claim it. This change does likely slightly reduce the number of random ports and therefore the protection from reply spoofing. The older behavior can be restored using the min-port and max-port config switches should that be a concern. - Scale the size of the DNS random-port pool based on the value of the
dns-forward-maxconfiguration. - TFTP tweak: Check sender of all received packets, as specified in RFC 1350 para 4.
- Fix problem with DNS retries in earlier versions.
Web CHANGELOG
- Add details to adlist table #1673 (@DL6ER)
- Don’t count new status types as blocked queries in long-term data #1743 (@yubiuser)
- Add hint for update command & documentation link #1749 (@j15e)
- Add Pi-hole darker theme #1731 (@DL6ER)
- Trim CNAME target input field value data #1759 (@Yrlish)
Core CHANGELOG
- Visual tweaks to blockpage #4036 (@Cafetier)
- Match wildcard regex used in the admin UI #3982 (@andras-tim)
pihole -gshould respose GRAVITYDB in pihole-FTL.conf #4086 (@DL6ER)- Fix pihole -g -r #4070 (@DL6ER)
- Add hostname to teleporter backup file if called from cli #4049 (@yubiuser)
- Fix issue with multipe default gateways when running the debug #4021 (@Flashbang007)
- Fix error trying to access undefined variables on splash page. #4095 (@jbaez)
- Improve regexes for IPv4 matching #4083 (@jbzdarkid)
- Fedora 33 Support #4004 (@bcambl)



Comments are closed.