Understanding DNSSEC validation using Pi-hole’s Query Log
The Domain Name System Security Extensions (DNSSEC) is an Internet standard that adds security mechanisms to the Domain Name System (DNS). It ensures both the authenticity and integrity of the DNS data. From FTL v5.9 on, Pi-hole shows and analyzes the internally generated DNSSEC queries needed to build the chain-to-trust. This feature is enabled by default and can be useful to provide additional details about DNSSEC transactions.
A (local) DNS resolver can use DNSSEC to verify that the DNS zone data it receives has not been modified and is indeed identical to the authoritative zone. DNSSEC was developed mainly as means against cache poisoning. It secures the transmission of resource records by means of digital signatures using asymmetric so-called public-key cryptography. If you are not familiar with the concept, think of it as a cleverly designed lock, where one key locks and one key unlocks. In DNSSEC, you get the unlocking public key, while the locking key is kept private. The owners of the authoritative server on which the zone to be secured is located signs each individual record using their private keys. DNS clients can validate this signature with the owner’s public key to verify said authenticity and integrity.
Technical details
A separate zone signing key (a pair consisting of a public and private key) is generated for each zone to be secured. The public part of the zone key is included in the zone file as a DNSKEY resource record. The private key is used to digitally sign each individual record of this zone. For this purpose, a new record type is provided, the RRSIG Resource Record, which contains the signature to the associated DNS record. For each transaction, the associated RRSIG record is supplied in addition to the actual resource record. The requesting resolver can then validate the signature using the public zone key.
DNSKEY records are used to propagate public keys through DNS: The owner of the key stores it as DNSKEY record on a publicly accessible DNS server. Anyone who needs this public key sends a corresponding DNSKEY request. You receive the public key in response. The procedure thus corresponds to any other DNS requests, for instance ordinary IP addresses. In practice, however, this type of propagation is not sufficient, since a complete zone could be forged. The public key must therefore either be introduced manually into the resolver as a trusted key or the associated DS resource record must be published in the overlying zone. The trusted key of the root zone (the uppermost level of the DNS hierarchy) is known by your Pi-hole and is hard-coded.
For a complete picture, we also need DS (Delegation Signer) records. Those are used to chain DNSSEC-signed zones. This allows multiple DNS zones to be combined into a chain of trust and validated via a single public key. The basic idea is to chain all the zones involved and use only the topmost one as the secure entry point. The security-providing and critical part is that DS record can be calculated from the DNSKEY, but not vice versa thanks to the used asynchronous cryptography.
How does verification work?
Example of a signed A record (requested on Nov 30, 2021):
$ dig +dnssec A www.pi-hole.net
[...]
;; ANSWER SECTION:
www.pi-hole.net. 3600 IN CNAME pi-hole.net.
www.pi-hole.net. 3600 IN RRSIG CNAME # Signed record type is CNAME
13 # Hash type (in this case ECDSAP256-SHA256)
3 # Signed name consists of three labels ("www", "pi-hole" and "net")
3600 # Original TTL
20211229232302 # Not valid after 2021-12-29 23:23:02
20211129232302 # Not valid before 2021-11-29 23:23:02
36126 # Unique number/key tag
pi-hole.net. # Name of the signer
+x/jPBz4Yyhnkb/b1dze3Sz4WhEhyk4/bs38Zjpo67Ep1fLmj8KLR1CE qpNMBpG/Y+29SYma4sDTF+pvMk4fHQ== # The hash
pi-hole.net. 300 IN A 3.18.136.52
pi-hole.net. 300 IN RRSIG A # Signed record type is A
13 # Hash type (in this case ECDSAP256-SHA256)
2 # Signed name consists of two labels ("pi-hole" and "net")
300 # Original TTL
20211229232302 # Not valid after 2021-12-29 23:23:02
20211129232302 # Not valid before 2021-11-29 23:23:02
36126 # Unique number/key tag
pi-hole.net. # Name of the signer
LGyR9ZHaH6UUO3KK7y6lwxzIbe3KbwQ9mzkaH+LZQLA+XJBfM2Vc5Bbd SWoYMOq063qUd0GYRDDCzrWjEvQVtQ== # The hash
When the validating resolver queries for pi-hole.net, it receives both the record itself (CNAME pi-hole.net and A 3.18.136.52) and the digital signatures (RRSIG CNAME 13 2 3600 ... and RRSIG A 13 2 300 ...). The digital signature records contain the ID of the used hash function (in our example, 13 = SHA256). Your Pi-hole can take the plain-text message (A 3.18.136.52) and run it through SHA-256 to produce a hashed value itself. The validating resolver then obtains the public key (DNSKEY records), decrypts the digital signature, and gets back the original hashed value produced by the authoritative server. If both hash values are identical, the answer is valid, meaning this answer came from the authoritative server (authenticity), and the content remained intact during transit (integrity).
This verification is repeated for every component up to the root zone of the DNS system to build the chain of trust. Furthermore, the validating resolver’s current system time needs to fall between the two not-valid-after and not-valid-before timestamps. If it does not, the validation fails, because it could be an attacker replaying an old captured answer set from the past, or feeding us a crafted one with incorrect future timestamps. This is the most often seen issue with DNSSEC validation on devices lacking a reliable clock (such as the widely used Raspberry Pi’s without a real-time clock (RTC) extension).
If the answer passes both the hash value check and the timestamp check, it is validated and the response is sent to the client; if it does not verify, a SERVFAIL is returned to the client instead of any records.
Examples
We will shortly mention what is going on using three simple examples for typical DNSSEC results you may see in your Pi-hole’s Query Log:
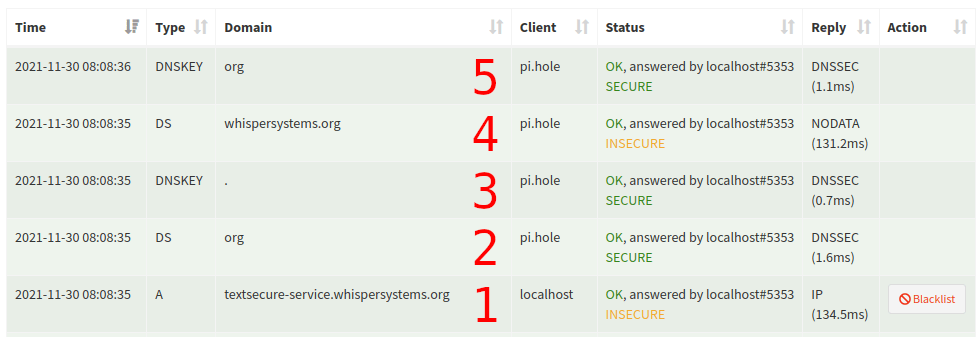
sigok.verteiltesysteme.net (DNSSEC test domain) – SECURE
- Client
localhostrequestsA sigok.verteiltesysteme.net– the server responds with theArecord and threeRRSIG(one for the A, the AAAA and the NSEC records of this domain) DS netis requested – the server responds with theDSrecord and the associatedRRSIG- The root zone key (
DNSKEY .) is requested, the reply type isDNSSEC– the server responds with theDNSKEYof the root zone and itsRRSIG DS verteiltesysteme.netis requested – the server responds with theDSrecord and the associatedRRSIGDNSKEY netis requested, the reply type isDNSSEC– the server responds with theDNSKEYofnetand itsRRSIGDNSKEY verteiltesysteme.netis requested – the server responds with theDNSKEYofverteiltesysteme.netand itsRRSIG
Pi-hole verifies the A record for sigok.verteiltesysteme.net the following way:
- The
ArecordA sigok.verteiltesysteme.net(reply #1) is validated through itsRRSIG(in same reply) using theDNSKEYofverteiltesysteme.net(reply #6) - The
DNSKEYofverteiltesysteme.net(reply #6) is validated through itsRRSIGusing theDSofverteiltesysteme.net(reply #4) - The
DNSKEYofnet(reply #5) is validated through itsRRSIGusing theDSofnet(reply #2) - The
DNSKEYof the root zone (reply #3) is validated through itsRRSIGusing the trust-anchor hard-wired into Pi-hole
The result is SECURE as Pi-hole successfully build the chain of trust up from the queried domain to the (known) root zone.
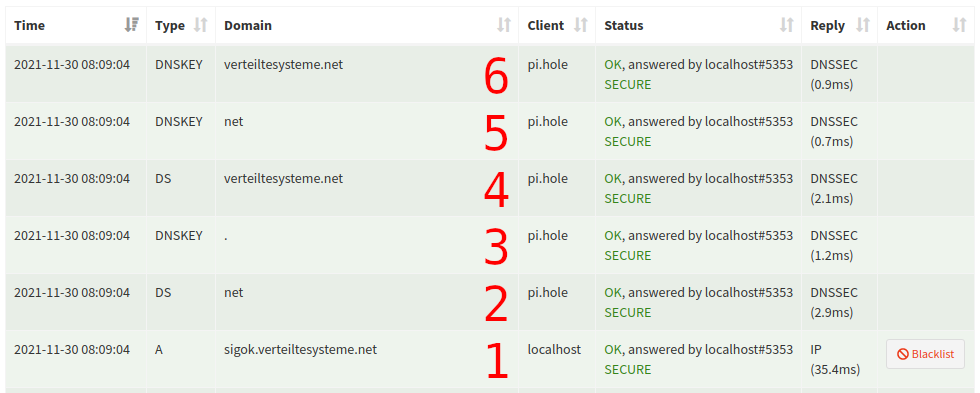
textsecure-service.whispersystems.org (Signal messenger) – INSECURE
- Client
localhostrequeststextsecure-service.whispersystems.org– the server responds with theArecord and itsRRSIG DS orgis requested – the server responds with theDSrecord and the associatedRRSIG- The root zone key (
DNSKEY .) is requested – the server responds with theDNSKEYof the root zone and itsRRSIG DS whispersystems.orgis requested (at theorgDNS server), the reply isNODATA, the autoritative server also appends some other informationDNSKEY orgis requested – the server responds with theDNSKEYrecord and the associatedRRSIG
Note the absence of a sixth query for DNSKEY whispersystems.org. As DS whispersystems.org returned NODATA, we already know that the entire zone whispersystems.org is not DNSSEC-signed.
Pi-hole verifies the A record for textsecure-service.whispersystems.org the following way:
- The
ArecordA textsecure-service.whispersystems.org(reply #1) does not containRRSIG– it is not signed. To rule out possible manipulation that might be going on (a malicious server may just have stripped theRRSIG), Pi-hole continues building the chain of trust DSofwhispersystems.org(reply #4) contains additional information (NSEC3and correspondingRRSIG) to prove the non-existence of aDSrecord for this zone- The
DNSKEYoforg(reply #5) is validated through itsRRSIGusing theDSoforg(reply #2) - The
DNSKEYof the root zone (reply #3) is validated through itsRRSIGusing the root zone’s trust-anchor known by Pi-hole
The result is INSECURE as Pi-hole successfully verified the non-existence of DS whispersystems.org . This verified the absence of DNSSEC signing for the entirety of whispersystems.org .
If you want to learn more about the tricky business of authenticated denial of existence in DNS, check out RFC 7129.
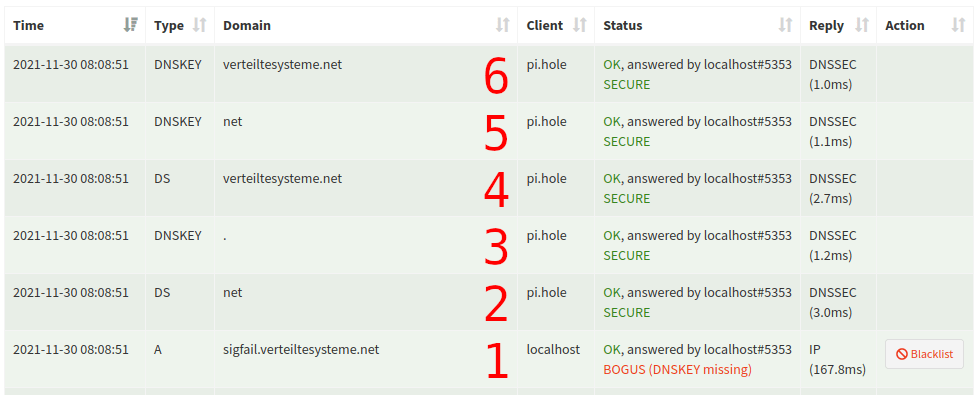
sigfail.verteiltesysteme.net (DNSSEC test domain) – BOGUS
- Client
localhostrequestsA sigfail.verteiltesysteme.net– the server responds with theArecord and threeRRSIG(one for the A, the AAAA and the NSEC records of this domain) DS netis requested – the server responds with theDSrecord and the associatedRRSIG- The root zone key (
DNSKEY .) is requested, the reply type isDNSSEC– the server responds with theDNSKEYof the root zone and itsRRSIG DS verteiltesysteme.netis requested – the server responds with theDSrecord and the associatedRRSIGDNSKEY netis requested, the reply type isDNSSEC– the server responds with theDNSKEYofnetand itsRRSIGDNSKEY verteiltesysteme.netis requested – the server responds with theDNSKEYofverteiltesysteme.netand itsRRSIG
Pi-hole verifies the A record for sigfail.verteiltesysteme.net the following way:
- The
ArecordA sigfail.verteiltesysteme.net(reply #1) cannot be validated through itsRRSIG(in same reply) – as the computed hash is not the same as the hash decrypted with theDNSKEYofverteiltesysteme.net(reply #6) - The
DNSKEYofverteiltesysteme.net(reply #6) is validated through itsRRSIGusing theDSofverteiltesysteme.net(reply #4) - The
DNSKEYofnet(reply #5) is validated through itsRRSIGusing theDSofnet(reply #2) - The
DNSKEYof the root zone (reply #3) is validated through itsRRSIGusing the trust-anchor hard-wired into Pi-hole
The result is BOGUS as the A sigfail.verteiltesysteme.net is not signed by any trusted key even though DNSSEC is enabled for this zone.
Other DNSSEC test domains result in the following BOGUS codes:
- dnssec-failed.org: BOGUS (DNSKEY missing)
- None of the 2
DNSKEY dnssec-failed.orgrecords could be validated by any of the 2DS dnssec-failed.orgrecords. - The
DNSKEY dnssec-failed.orgwas not signed by any trusted keys and, hence, rejected.
- None of the 2
- rhybar.cz: BOGUS (DNSSEC signature expired)
RRSIG rhybar.cz: The Signature Expiration field of theRRSIGrecord is in the past (2008-10-30 08:00:58+00:00).
If your selected upstream does not provide any reasons, Pi-hole can only show BOGUS (refused upstream). In this case, the upstream server is rejecting the query without providing any further details. Your Pi-hole cannot analyse what went wrong.
By default, a local unbound instance as upstream resolver will not provide any details. To enable the full validation inside Pi-hole, you have to add
# Does not actually turn off DNSSEC, but stops the resolver from
# withholding bogus answers from clients.
val-permissive-mode: yes
to the server section of your config file. However, be aware that this can void the protection provided by DNSSEC for devices querying unbound directly without using your Pi-hole. Hence, we do not recommend enabling permissive mode in production systems.
Comments are closed.